How To Use RemoteIoT Behind Firewall Using Mac Server Example
In today's interconnected world, leveraging IoT (Internet of Things) devices behind firewalls is a common challenge for IT professionals. The ability to securely access and manage remote IoT devices using a Mac server offers a unique solution that balances functionality with robust security measures. Understanding how to use RemoteIoT behind a firewall using a Mac server example is essential for organizations aiming to optimize their IoT infrastructure while ensuring data protection.
As more businesses adopt IoT technologies, the need for secure communication between devices grows exponentially. This article will guide you step-by-step on how to set up and configure RemoteIoT systems behind firewalls using a Mac server. By following this guide, you can ensure seamless integration of IoT devices into your network without compromising security.
Whether you're a network administrator, IT professional, or tech enthusiast, this article provides valuable insights into the technical aspects of managing IoT devices in a secure environment. Let's dive into the details and explore how to achieve this effectively.
Read also:Ultimate Guide To Movierulz 2024 Ullu Web Series Download And More
Table of Contents
- Introduction to RemoteIoT and Firewalls
- Mac Server Overview
- Setting Up Mac Server for IoT
- Firewall Considerations
- Securing RemoteIoT Connections
- Step-by-Step Guide to Configure
- Common Issues and Solutions
- Best Practices for IoT Security
- Performance Optimization Tips
- Conclusion and Call to Action
Introduction to RemoteIoT and Firewalls
RemoteIoT refers to the ability to manage and interact with IoT devices remotely, even when they are located behind firewalls. Firewalls are essential for protecting internal networks from unauthorized access, but they can also create barriers for legitimate remote connections. Understanding how to configure a Mac server to facilitate secure RemoteIoT connections is crucial for modern IT infrastructures.
Why Use a Mac Server?
Mac servers provide a stable and secure platform for managing IoT devices. They offer a range of features that make them ideal for this purpose, including:
- Advanced security protocols
- Easy integration with macOS devices
- Robust performance capabilities
By leveraging a Mac server, organizations can ensure that their IoT devices remain accessible while maintaining a high level of security.
Mac Server Overview
A Mac server is a powerful tool for managing and securing IoT devices. It provides a centralized platform for configuring and monitoring devices, making it easier to manage complex networks. The server can be configured to handle various tasks, including data storage, network management, and security monitoring.
Key Features of Mac Server
Here are some key features of a Mac server that make it suitable for managing IoT devices:
- Support for multiple users and devices
- Advanced encryption and security protocols
- Integration with cloud services
These features make the Mac server an excellent choice for organizations looking to implement secure RemoteIoT solutions.
Read also:John Cusack Partner The Definitive Guide To His Collaborations Relationships And Career
Setting Up Mac Server for IoT
Setting up a Mac server for IoT involves several steps. First, you need to install the server software on your Mac. Then, configure the necessary settings to ensure compatibility with your IoT devices.
Steps to Set Up
Follow these steps to set up your Mac server:
- Install macOS Server software
- Configure network settings
- Set up user accounts and permissions
- Enable IoT device integration
Each step is critical for ensuring that your server is properly configured to handle IoT devices.
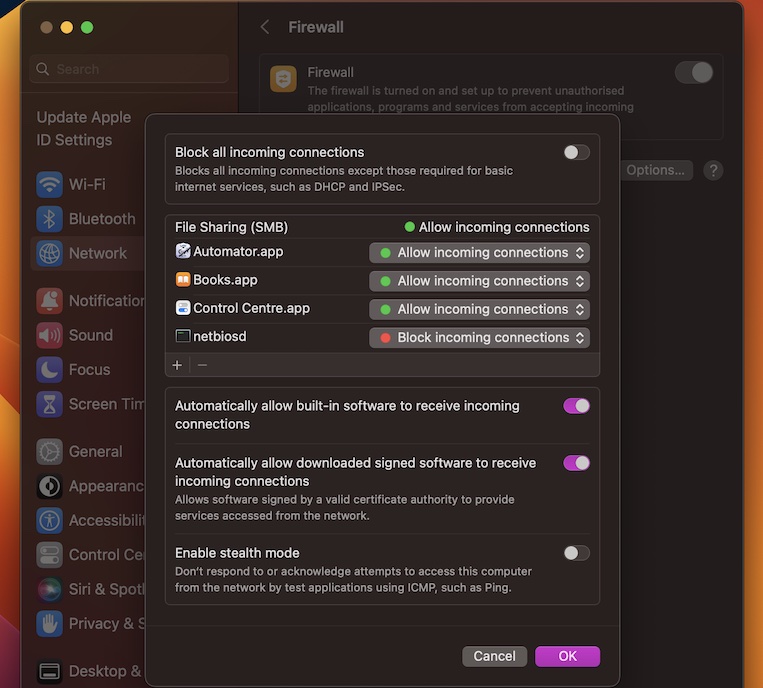
Firewall Considerations
When setting up RemoteIoT behind a firewall, it's essential to consider the security implications. Firewalls are designed to block unauthorized access, but they can also interfere with legitimate connections. Proper configuration is necessary to allow secure communication between the server and IoT devices.
Configuring Firewall Rules
To configure your firewall for RemoteIoT, follow these guidelines:
- Identify the necessary ports for communication
- Create specific rules to allow traffic from trusted sources
- Monitor firewall logs for suspicious activity
These steps will help ensure that your firewall does not block legitimate connections while still providing robust security.
Securing RemoteIoT Connections
Security is paramount when managing IoT devices remotely. Implementing strong security measures is essential to protect sensitive data and prevent unauthorized access.
Best Security Practices
Here are some best practices for securing RemoteIoT connections:
- Use strong encryption protocols
- Implement multi-factor authentication
- Regularly update software and firmware
By following these practices, you can significantly enhance the security of your RemoteIoT setup.
Step-by-Step Guide to Configure
Here’s a step-by-step guide to configuring a Mac server for RemoteIoT behind a firewall:
Step 1: Install macOS Server
Begin by installing the macOS Server software on your Mac. This will provide the necessary tools for managing IoT devices.
Step 2: Configure Network Settings
Set up your network settings to ensure proper communication between the server and IoT devices. This includes configuring IP addresses and subnet masks.
Step 3: Set Up Firewall Rules
Create specific firewall rules to allow traffic from trusted sources while blocking unauthorized access.
Step 4: Enable IoT Device Integration
Finally, enable integration with your IoT devices to ensure they can communicate with the server securely.
Common Issues and Solutions
While setting up RemoteIoT behind a firewall, you may encounter several common issues. Here are some solutions to help you troubleshoot:
Issue 1: Connection Problems
If you experience connection issues, check your firewall settings and ensure that the necessary ports are open.
Issue 2: Security Breaches
To prevent security breaches, regularly update your server software and implement strong authentication measures.
Best Practices for IoT Security
Implementing best practices for IoT security is essential for protecting your network. Here are some tips:
- Regularly audit your network for vulnerabilities
- Limit access to sensitive data
- Use secure communication protocols
By following these practices, you can create a secure environment for managing IoT devices.
Performance Optimization Tips
Optimizing the performance of your Mac server is crucial for ensuring efficient IoT management. Here are some tips:
- Monitor server performance regularly
- Optimize network bandwidth usage
- Implement caching strategies
These tips will help you maintain optimal performance for your RemoteIoT setup.
Conclusion and Call to Action
In conclusion, managing RemoteIoT devices behind a firewall using a Mac server offers a secure and efficient solution for modern organizations. By following the steps outlined in this article, you can ensure that your IoT devices remain accessible while maintaining a high level of security.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our site for more insights into IoT and network security. Together, let's build a safer and more connected digital world!