Comprehensive Guide To RemoteIoT Monitoring SSH Download For Mac Free
RemoteIoT monitoring has become an essential solution for businesses and individuals looking to enhance their security, scalability, and efficiency in managing IoT devices. In today's digital era, the ability to remotely monitor and manage IoT systems is critical for maintaining operational integrity. Whether you're a tech enthusiast or a professional, understanding how to implement remote IoT monitoring using SSH on a Mac can significantly improve your workflow. This guide will walk you through everything you need to know about downloading and setting up remote IoT monitoring SSH for Mac free of charge.
As the world becomes increasingly connected, IoT devices are playing a pivotal role in revolutionizing industries. However, the challenge lies in securely managing these devices from remote locations. This is where SSH (Secure Shell) comes into play. SSH provides a secure and reliable way to connect to IoT devices over the internet, ensuring that your data remains protected while giving you full control over your systems.
Whether you're a beginner exploring remote IoT monitoring or an experienced professional seeking advanced solutions, this comprehensive guide will equip you with the knowledge and tools necessary to set up SSH for remote IoT monitoring on your Mac device. Let's dive in!
Read also:Ullu Movierulz Your Ultimate Guide To The Trending Entertainment Platform
Table of Contents
- Introduction to RemoteIoT Monitoring
- Understanding SSH Basics
- Why Use SSH for RemoteIoT Monitoring?
- Mac OS Support for SSH
- How to Download SSH for Mac
- Setting Up RemoteIoT Monitoring with SSH
- Best Practices for Secure RemoteIoT Monitoring
- Troubleshooting Common Issues
- Benefits of Using SSH for RemoteIoT Monitoring
- Future Trends in RemoteIoT Monitoring
Introduction to RemoteIoT Monitoring
RemoteIoT monitoring refers to the process of supervising and managing IoT devices from a distant location. This technology allows users to access, control, and analyze data from IoT devices without being physically present. The primary goal of remote IoT monitoring is to enhance operational efficiency, reduce costs, and improve decision-making capabilities.
With the increasing number of IoT devices being deployed worldwide, the demand for secure and scalable remote monitoring solutions has surged. RemoteIoT monitoring SSH download for Mac offers a seamless way to connect to these devices securely, making it an ideal choice for both personal and professional use.
Key benefits of remote IoT monitoring include real-time data access, enhanced security, and reduced downtime. By leveraging SSH, users can ensure that their IoT systems remain protected from unauthorized access while maintaining optimal performance.
Understanding SSH Basics
What is SSH?
SSH, or Secure Shell, is a cryptographic network protocol used to securely operate network services over an unsecured network. It provides strong authentication and encrypted data communications, ensuring that sensitive information remains protected during transmission.
SSH is widely used for remote command-line login and remote command execution, but it also supports tunneling, forwarding arbitrary TCP connections, and X11 connections. Its versatility makes it an invaluable tool for managing remote systems and applications.
How Does SSH Work?
SSH operates by establishing a secure connection between a client and a server. The client initiates the connection, and the server authenticates the client using either password-based or public key authentication. Once authenticated, the client can securely access the server's resources.
Read also:Best Remote Iot Behind Router For Raspberry Pi A Comprehensive Guide
- Encryption: SSH encrypts all data transmitted between the client and server, preventing eavesdropping and data tampering.
- Authentication: SSH uses robust authentication methods to verify the identity of both the client and server.
- Integrity: SSH ensures that data remains unaltered during transmission by using cryptographic checksums.
Why Use SSH for RemoteIoT Monitoring?
SSH is the preferred method for remote IoT monitoring due to its robust security features and ease of use. Here are some reasons why SSH is ideal for managing IoT devices:
- Secure Data Transmission: SSH encrypts all data transmitted between the client and server, ensuring that sensitive information remains protected.
- Strong Authentication: SSH supports multiple authentication methods, including password-based and public key authentication, providing enhanced security.
- Scalability: SSH can handle multiple connections simultaneously, making it suitable for managing large-scale IoT deployments.
- Compatibility: SSH is compatible with a wide range of devices and operating systems, including Mac, ensuring seamless integration with existing infrastructure.
Mac OS Support for SSH
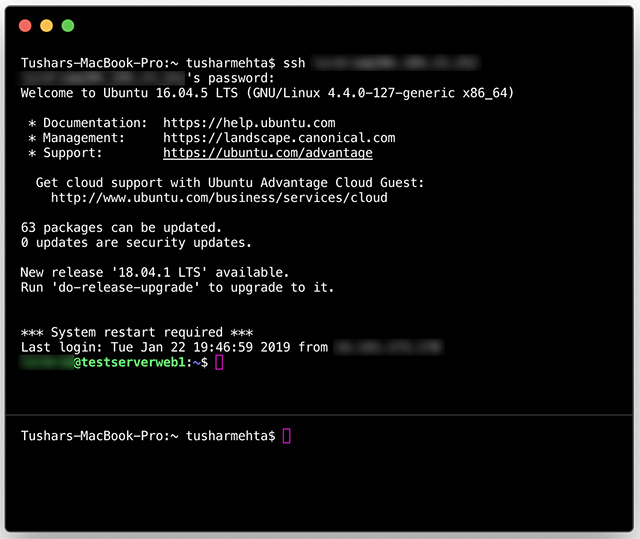
Mac OS comes with built-in support for SSH, making it easy for users to set up remote IoT monitoring without requiring additional software. The Terminal application, which is included with every Mac, provides a powerful interface for executing SSH commands.
To access SSH on your Mac, simply open the Terminal application and type the following command:
ssh [username]@[hostname]
Replace [username] with your IoT device's username and [hostname] with its IP address or domain name. Once connected, you can execute commands to manage and monitor your IoT devices.
How to Download SSH for Mac
While Mac OS includes SSH by default, there may be instances where you need to download additional tools or software to enhance your remote IoT monitoring capabilities. Here's how you can download SSH-related tools for your Mac:
Using Homebrew
Homebrew is a popular package manager for Mac that allows you to easily install and manage software. To install SSH-related tools using Homebrew, follow these steps:
- Install Homebrew by running the following command in Terminal:
- brew install openssh
Alternative SSH Clients
If you prefer a graphical user interface (GUI) over the command-line interface, consider using alternative SSH clients such as:
- Termius: A cross-platform SSH client with a user-friendly interface.
- SecureCRT: A powerful SSH client offering advanced features for remote management.
- PuTTY (for Mac): A free and open-source SSH client that supports multiple protocols.
Setting Up RemoteIoT Monitoring with SSH
Step 1: Prepare Your IoT Device
Before setting up remote IoT monitoring, ensure that your IoT device is properly configured to accept SSH connections. This typically involves enabling SSH on the device and setting up a secure password or public key authentication.
Step 2: Connect to Your IoT Device
Using the Terminal application on your Mac, connect to your IoT device by typing the following command:
ssh [username]@[hostname]
Replace [username] and [hostname] with your device's credentials. If prompted, accept the server's key and enter your password or private key to complete the connection.
Step 3: Monitor and Manage Your IoT Device
Once connected, you can execute commands to monitor and manage your IoT device. Common commands include:
- top: Displays real-time system performance metrics.
- df -h: Shows disk usage information.
- ping [hostname]: Tests network connectivity to a specific host.
Best Practices for Secure RemoteIoT Monitoring
To ensure the security and reliability of your remote IoT monitoring setup, follow these best practices:
- Use Strong Passwords: Always use strong, unique passwords for your IoT devices and SSH accounts.
- Enable Public Key Authentication: Disable password-based authentication and use public key authentication for added security.
- Limit SSH Access: Restrict SSH access to specific IP addresses or networks to reduce the risk of unauthorized access.
- Keep Software Updated: Regularly update your SSH client and server software to patch security vulnerabilities.
Troubleshooting Common Issues
While setting up remote IoT monitoring with SSH on Mac is generally straightforward, you may encounter some issues. Here are solutions to common problems:
Connection Refused
If you receive a "Connection refused" error, ensure that:
- Your IoT device's SSH service is running.
- Firewall rules allow incoming SSH connections.
- You're using the correct hostname or IP address.
Authentication Failure
If authentication fails, verify that:
- Your username and password are correct.
- Public key authentication is properly configured.
- SSH keys are correctly exchanged between the client and server.
Benefits of Using SSH for RemoteIoT Monitoring
Using SSH for remote IoT monitoring offers numerous advantages, including:
- Enhanced Security: SSH provides robust encryption and authentication mechanisms to protect your IoT devices.
- Improved Efficiency: Remote monitoring allows you to manage IoT devices from anywhere, reducing the need for on-site visits.
- Cost Savings: By minimizing downtime and optimizing resource utilization, SSH-based remote monitoring can lead to significant cost savings.
Future Trends in RemoteIoT Monitoring
As technology continues to evolve, the future of remote IoT monitoring looks promising. Key trends to watch include:
- AI Integration: Artificial intelligence will play a crucial role in automating and optimizing IoT monitoring processes.
- 5G Connectivity: The rollout of 5G networks will enable faster and more reliable remote IoT monitoring.
- Edge Computing: Processing data closer to the source will reduce latency and improve real-time decision-making capabilities.
Conclusion
In conclusion, remote IoT monitoring using SSH download for Mac free is a powerful solution for managing IoT devices securely and efficiently. By following the steps outlined in this comprehensive guide, you can set up and maintain a robust remote monitoring system that meets your needs.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our site for more insights into remote IoT monitoring and related technologies. Together, let's embrace the future of connected devices and unlock their full potential!